
By Javier Medina ( X / LinkedIn)
Context and objective
USBCoercer is ESP32-S3 firmware that emulates a USB Ethernet adapter (NCM), serves DHCP and advertises WPAD (DHCP option 252) to direct to a PAC file. In addition, classless static routes (DHCP option 121) are provided to block victim’s host telemetry if necessary.
Think of USBCoercer as a “pocket LAN” that your PC trusts by default enough to ask, “what’s my proxy?”, so that when the interface appears, Microsoft Windows retrieves the USB offered PAC and applies the proxy rules. If the proxy challenges with NTLM, the system responds with the active security context allowing NTLM coercion. That context can be the logged-in user, a locked session, or the machine account before logging in.
The main goal is to capture or relay NTLM without touching the victim’s LAN on laptops and desktops running Microsoft Windows 10 and 11. Ultimately, this is a variant of the well-known WPAD spoofing attacks, based on physical access to the victim’s USB port.
Why USBCOERCER matters
Instead of influencing an existing network segment, the USB device exposes a private L2 link via USB that the host automatically configures. Windows lists it as a NIC using built-in NCM drivers, requests DHCP, consumes Option 252, retrieves the PAC, and applies it to WinINET/WinHTTP according to local policy. All of this occurs without user interaction and without the need for an open session.
It is also interesting to note that the USB device does not need to be the default route, so main device connectivity is not affected. Only if we want to block specific addresses or networks, such as telemetry nodes, can DHCP provide classless static routes (RFC 3442, Option 121), adding precise prefixes via the USB link without altering the main Internet route.
Lock screen and pre-logon
With the session locked, the USB NIC also is configured and services using WinHTTP can keep evaluating WPAD in user-locked scope. On the other hand, after a restart, if the USB device is inserted, exactly the same thing will happen before any user logs in, using the account’s machine context.
In both cases, after WPAD configuration, when the proxy responds with 407 and a NTLM challenge, Windows will negotiate and expose an appropriate response for capture or retransmission, the latter is conditional to protections such as EPA and signing on the target.
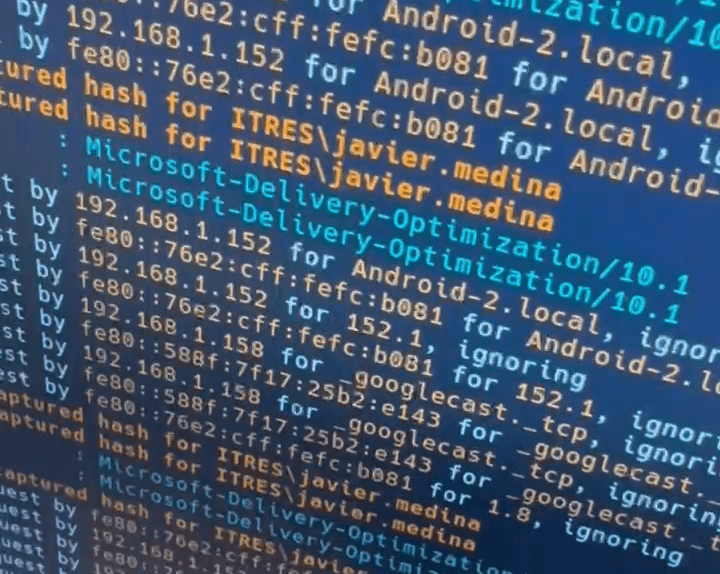
Verifying NTLM coercion
To verify NTLM Coercion use Windows 10/11 with automatic proxy detection enabled. Insert the USB stick and confirm the PAC injection when the LED turns “blue”.
Observe the PAC fetch on the HTTP server. Send a request through the proxy, return 407 Proxy Authentication Required with NTLM, and verify that the host responds in the current context (Responder will help here). Lock the session and repeat with a WinHTTP consumer to observe user-locked-scope behavior. Cold-boot with the stick inserted to check pre-logon activity with de account’s machine.
Limits and mitigation
When WPAD is disabled, or the proxy settings are fixed, the attack surface is reduced. Added to this is the fact that many modern applications incorporate protections that counter naive NTLM relaying, and also some terminal stacks block network class USB devices entirely.
For defenders, a sane baseline looks like this:
- Require an explicit HTTPS PAC at a fixed URL.
- Disable auto-proxy where you can.
- Set the WinHTTP proxy at machine scope via policy.
- Block USB NIC device classes.
Beyond prevention, detection is also important. That’s why we must look for unexpected USB NICs, DHCP options 252 and PAC recoveries in telemetry.
Release
We are launching USBCoercer as test firmware for M5Stack Atom S3U with a minimal DHCP+WPAD capability and the ability to serve a wpad.dat file via HTTP.
The intent is a compact USB-only path to force proxy policy on Windows, demonstrate that the effect reaches locked and machine contexts, and provide a clean baseline for NTLM capture and relay in offensive exercises with physical access to user equipment.
CREDITS AND PREVIOUS WORK
USBCoercer doesn’ t invent a new type of attack, but rather miniaturizes a known attack in simple, fast and linux-free ESP32-S3 firmware. It removes the cost and logistics that normally limit this technique while tapping into current concerns about DHCP route abuse (e.g. TunnelVision) and telemetry communications blocking.
Prior work (Fuller’s USB-Ethernet + Responder flow, P4wnP1, Bash Bunny) proved and inspired this idea; so the contribution is mostly operational. As an open-source, purpose-built implant it gives red teams a low-friction way to validate WPAD/WinHTTP and routing weaknesses; and also gives defenders a reproducible artifact to test and close those gaps.